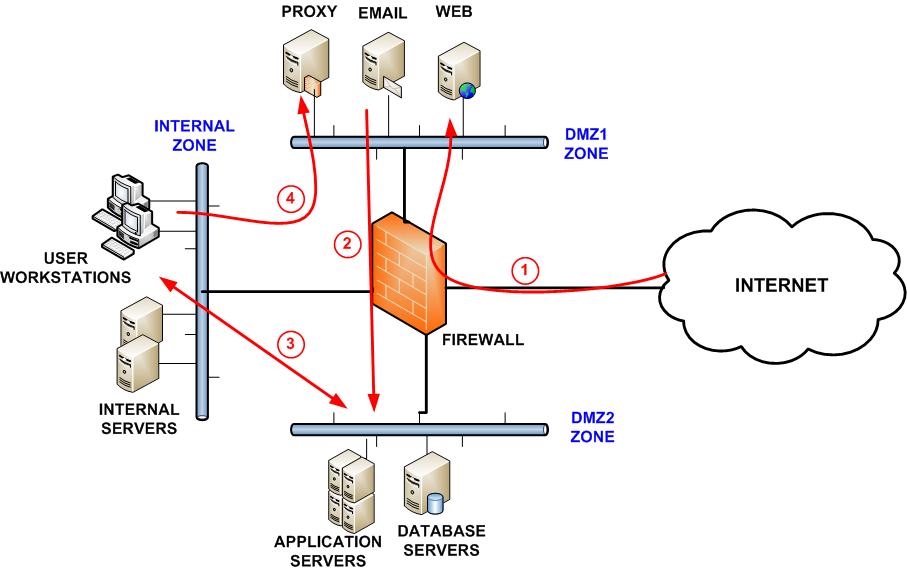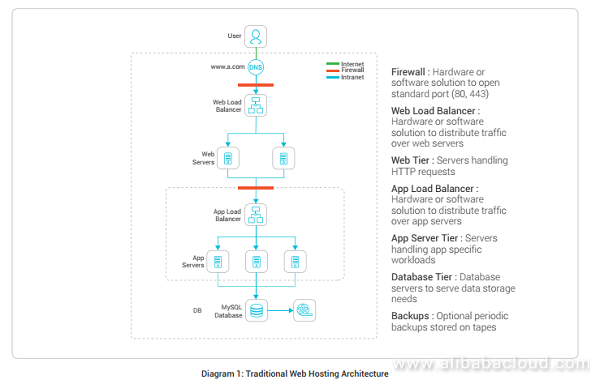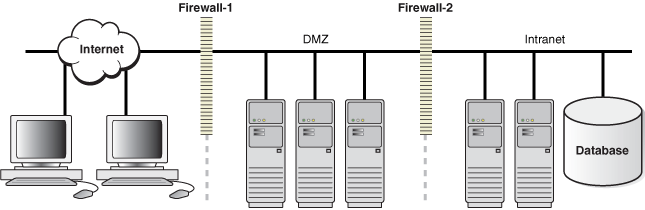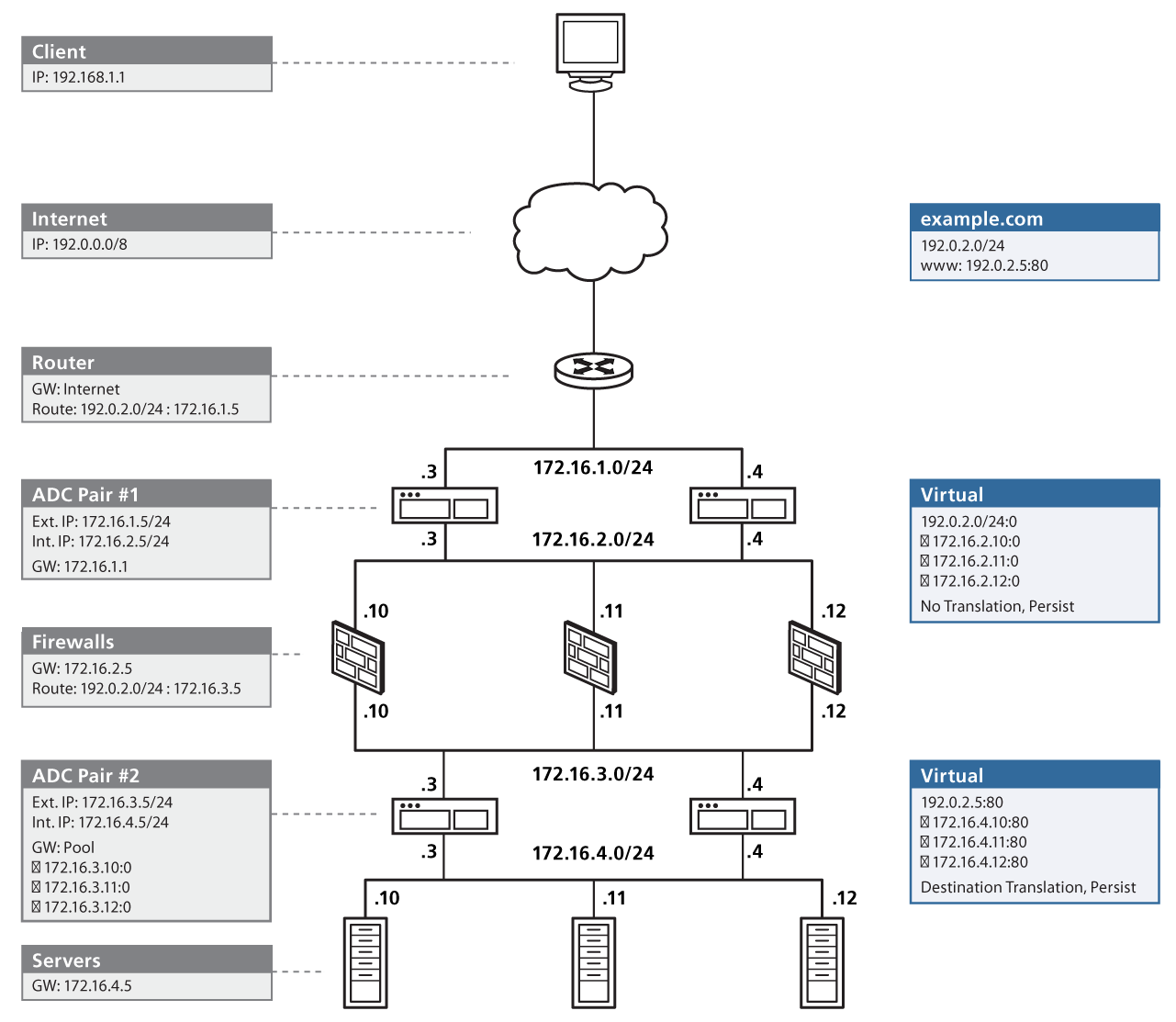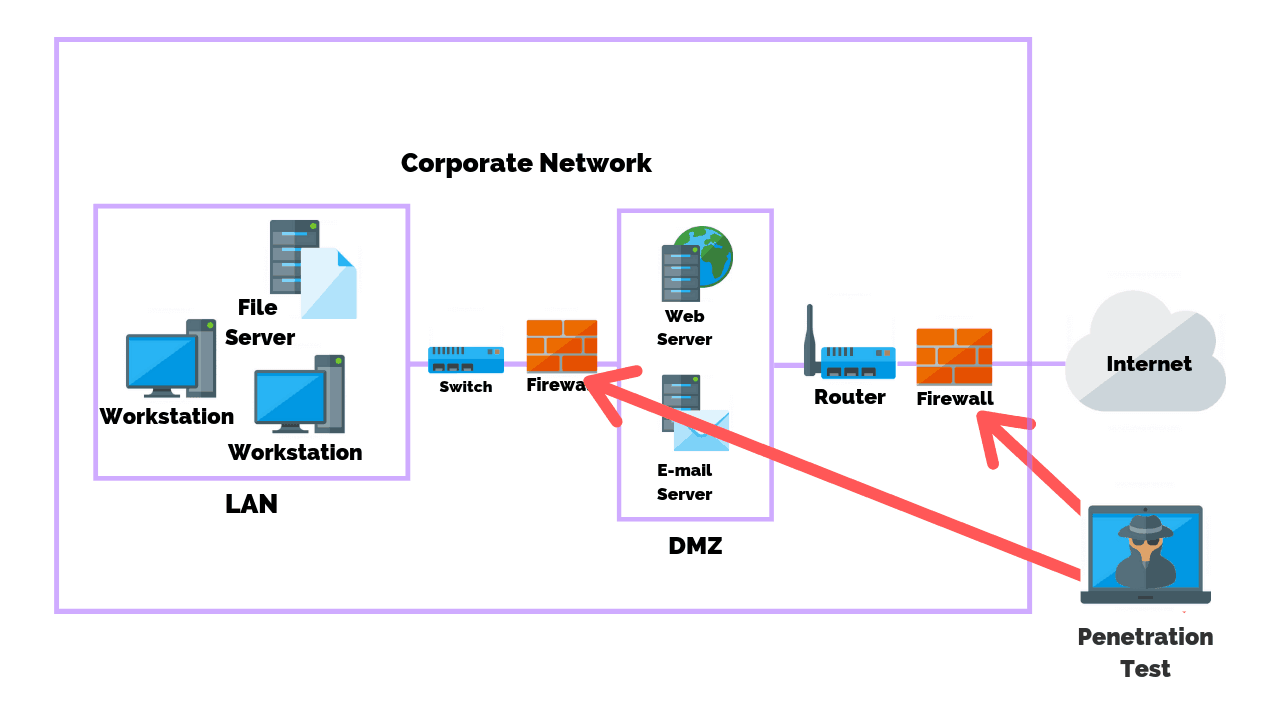
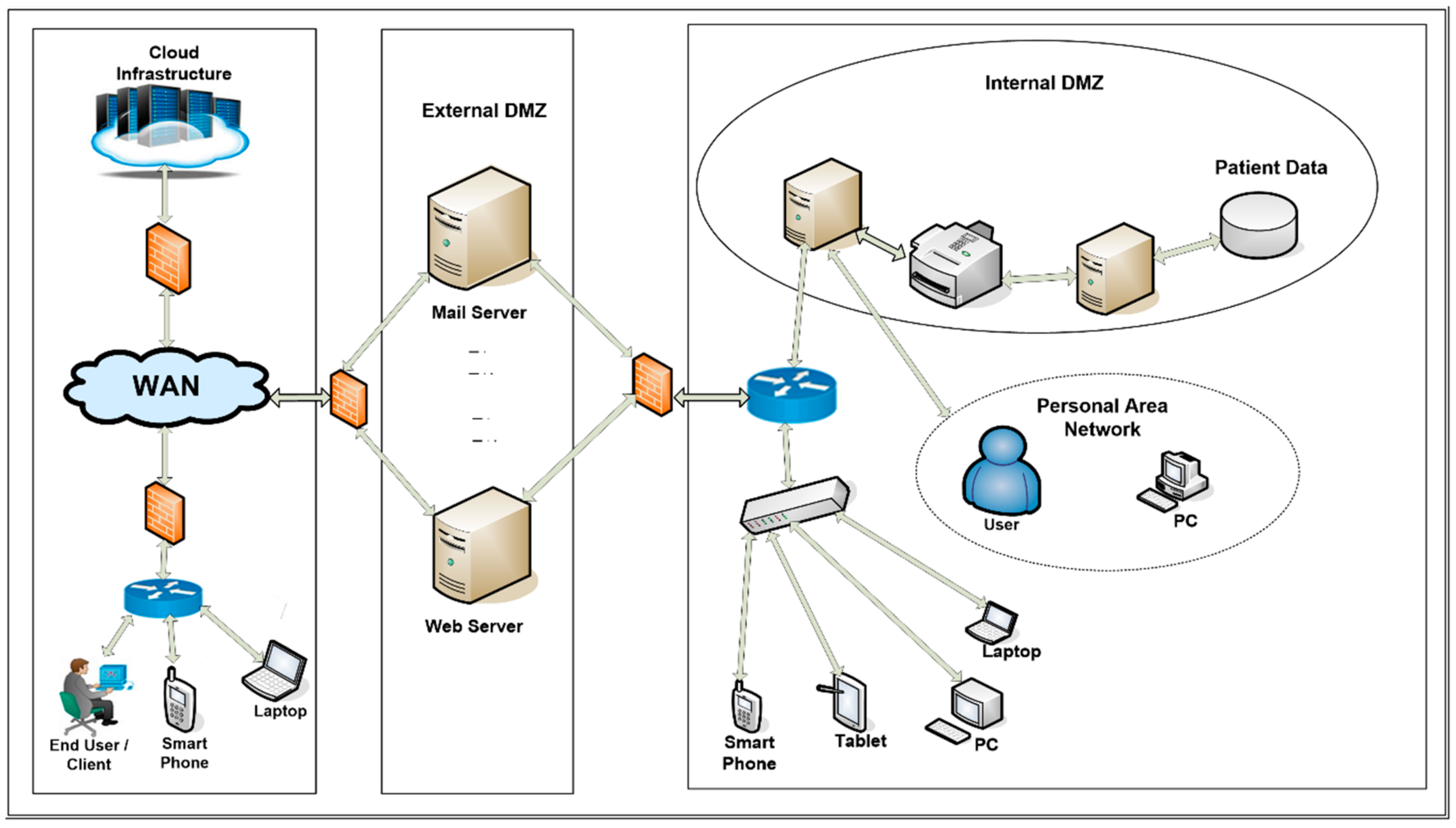
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML

Best practice for connecting publicly available server to internal LDAP/Active Directory? - Information Security Stack Exchange
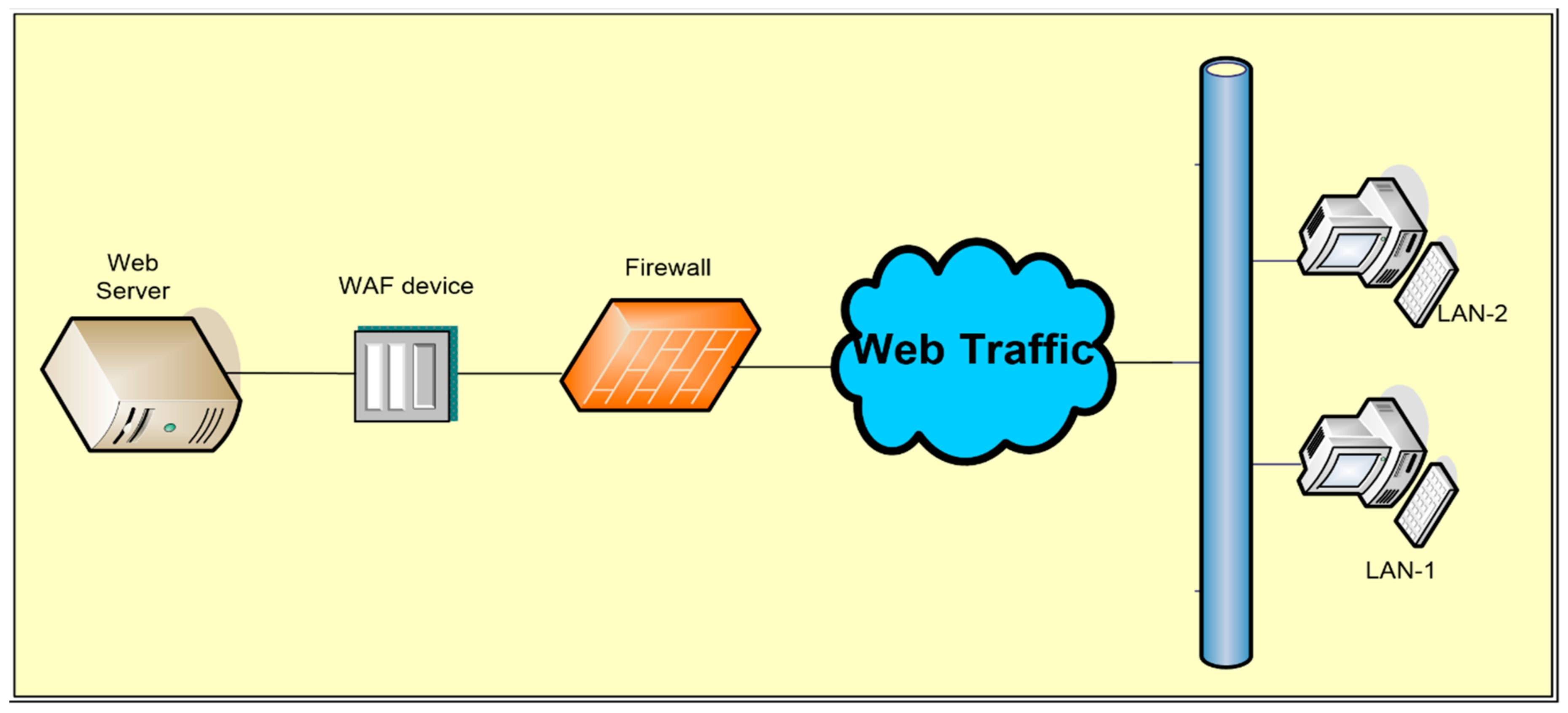
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
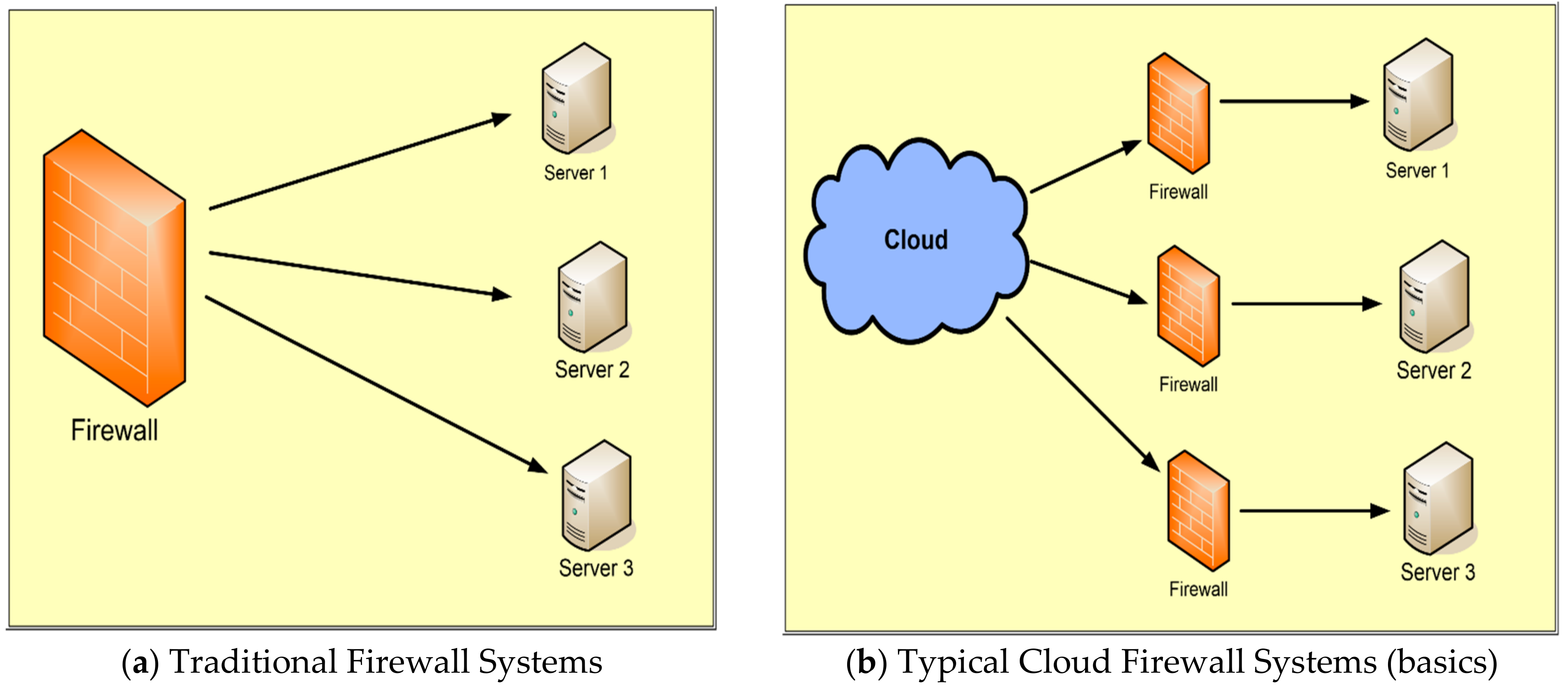
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review | HTML
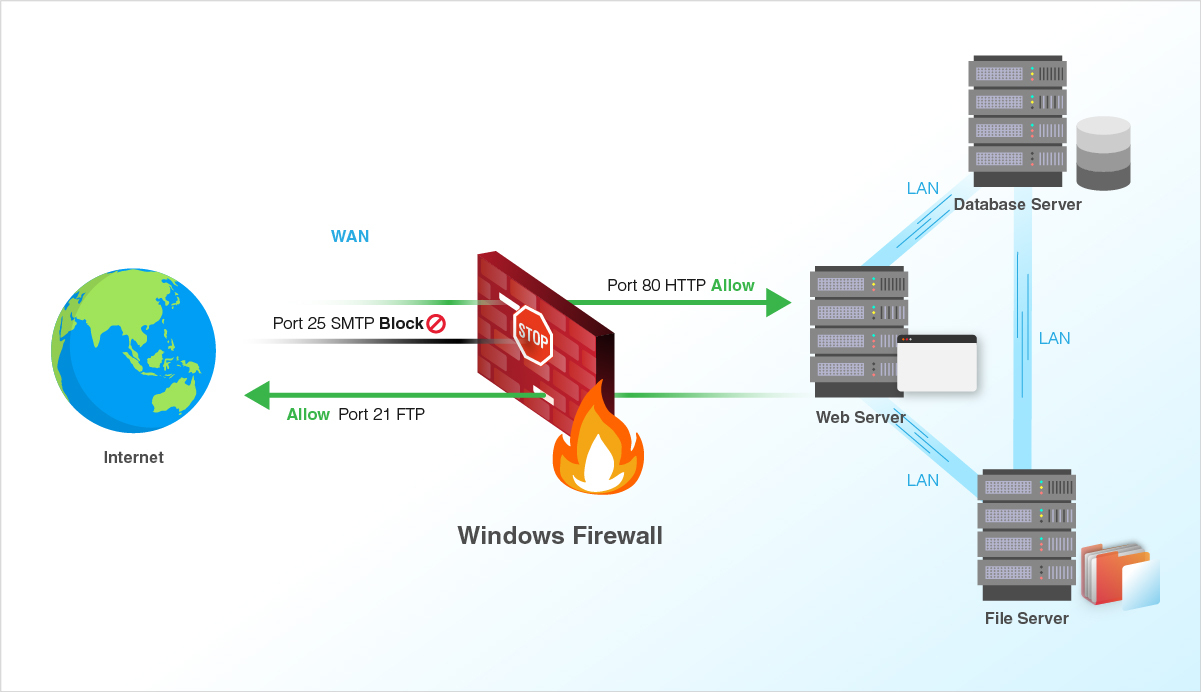
LayerStack Tutorials - LayerStack - Setting up Windows Firewall with Advanced Security on Windows Server 2019




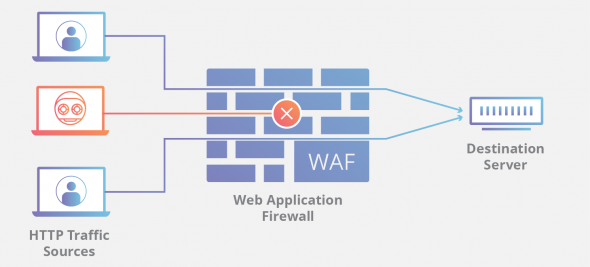


![Cisco SAFE Reference Guide - Enterprise Internet Edge [Design Zone for Security] - Cisco Cisco SAFE Reference Guide - Enterprise Internet Edge [Design Zone for Security] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/220001-230000/226001-227000/226654.eps/_jcr_content/renditions/226654.jpg)