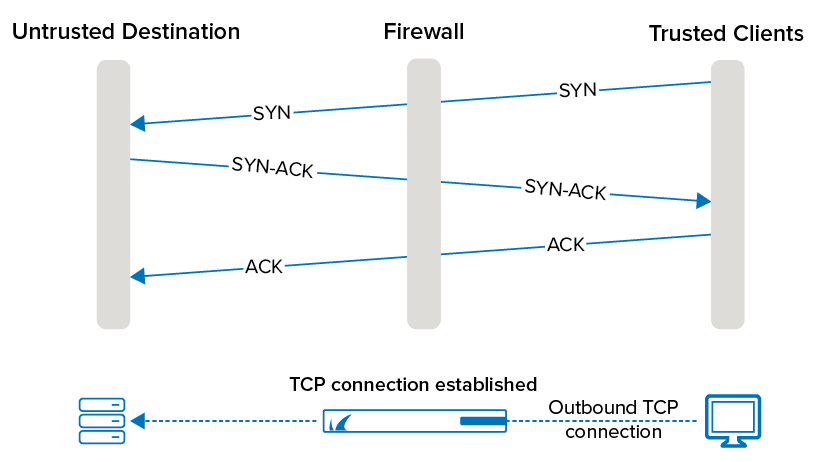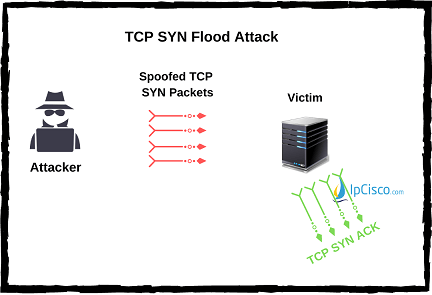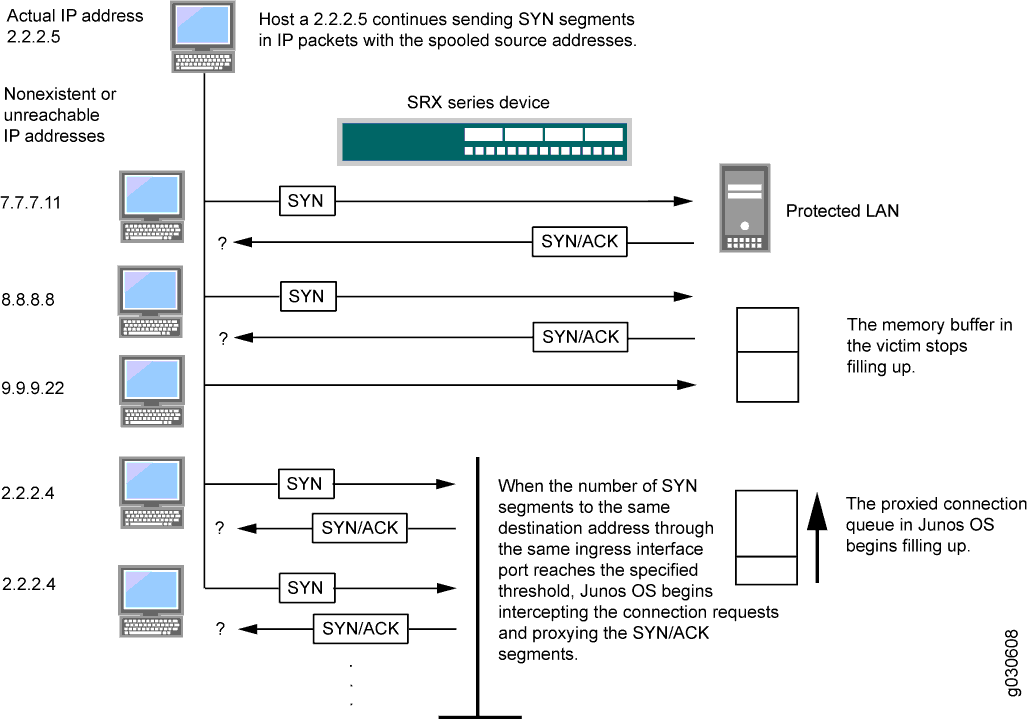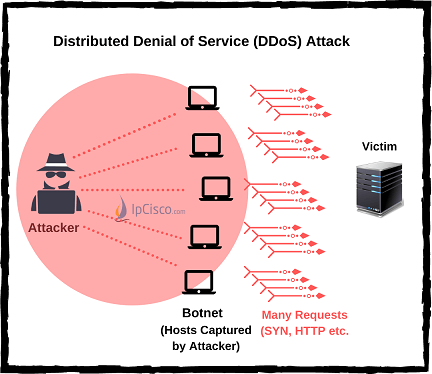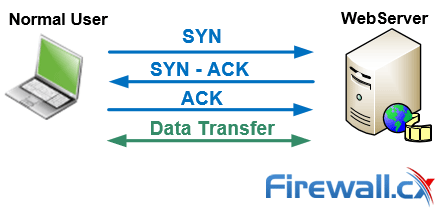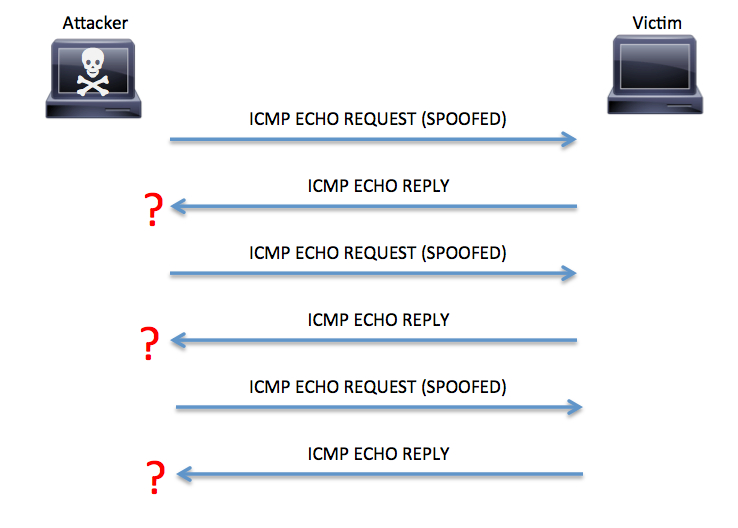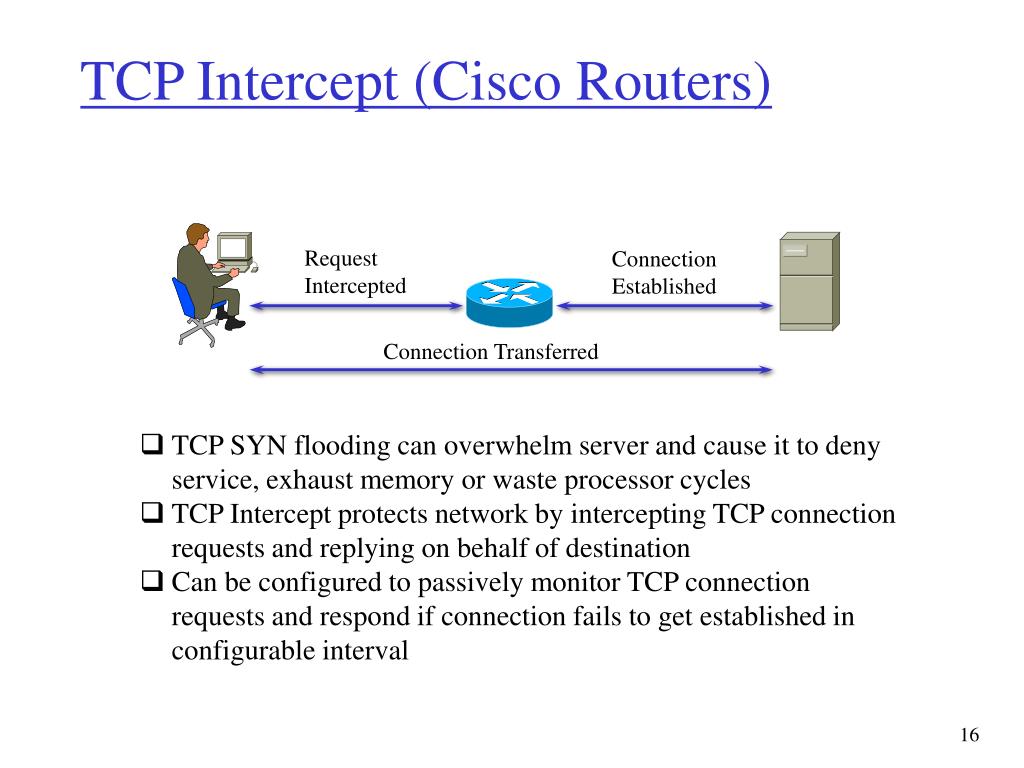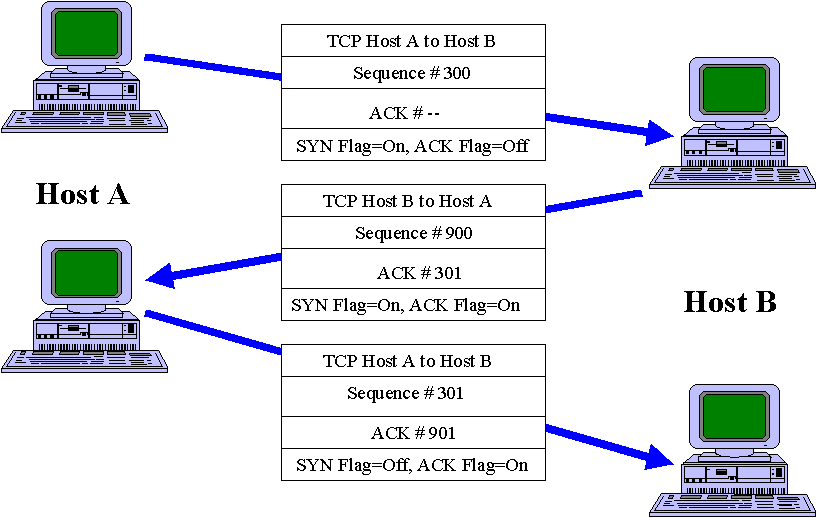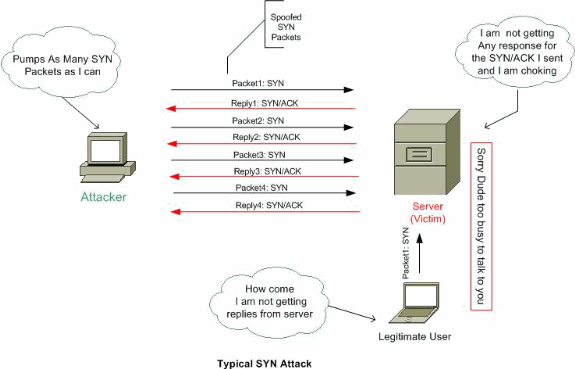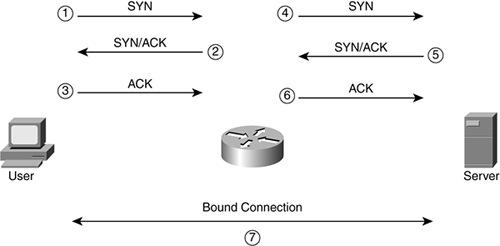
TCP Intercept :: Chapter 17. DoS Protection :: Part VII: Detecting and Preventing Attacks :: Router firewall security :: Networking :: eTutorials.org

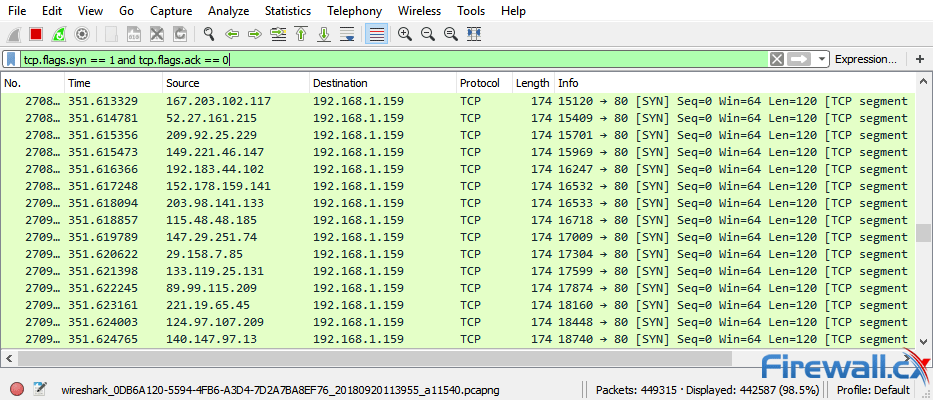
SYN flooding attack detection by TCP handshake anomalies - Bellaïche - 2012 - Security and Communication Networks - Wiley Online Library