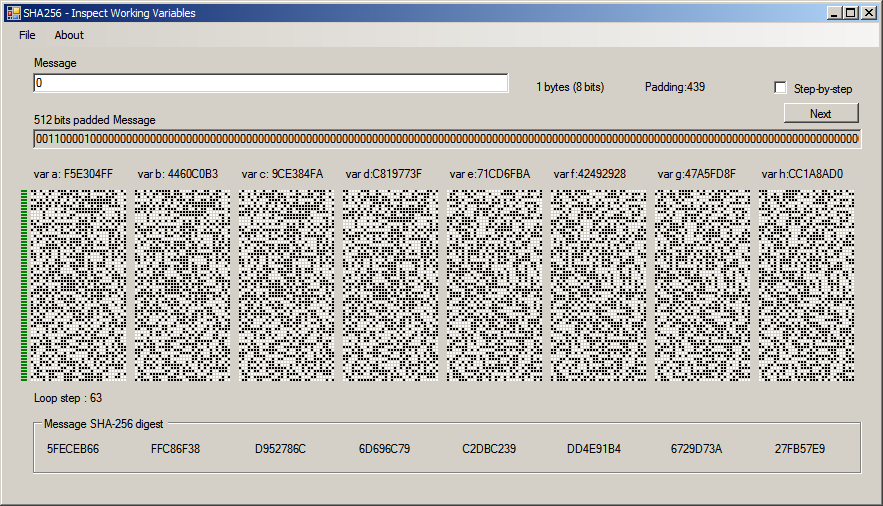
![Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net](https://edustorage.net/files/hashcat/cracked-sha256-pass.png?d00c4396d8)
Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net
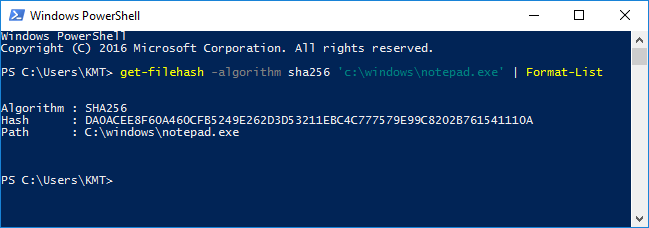
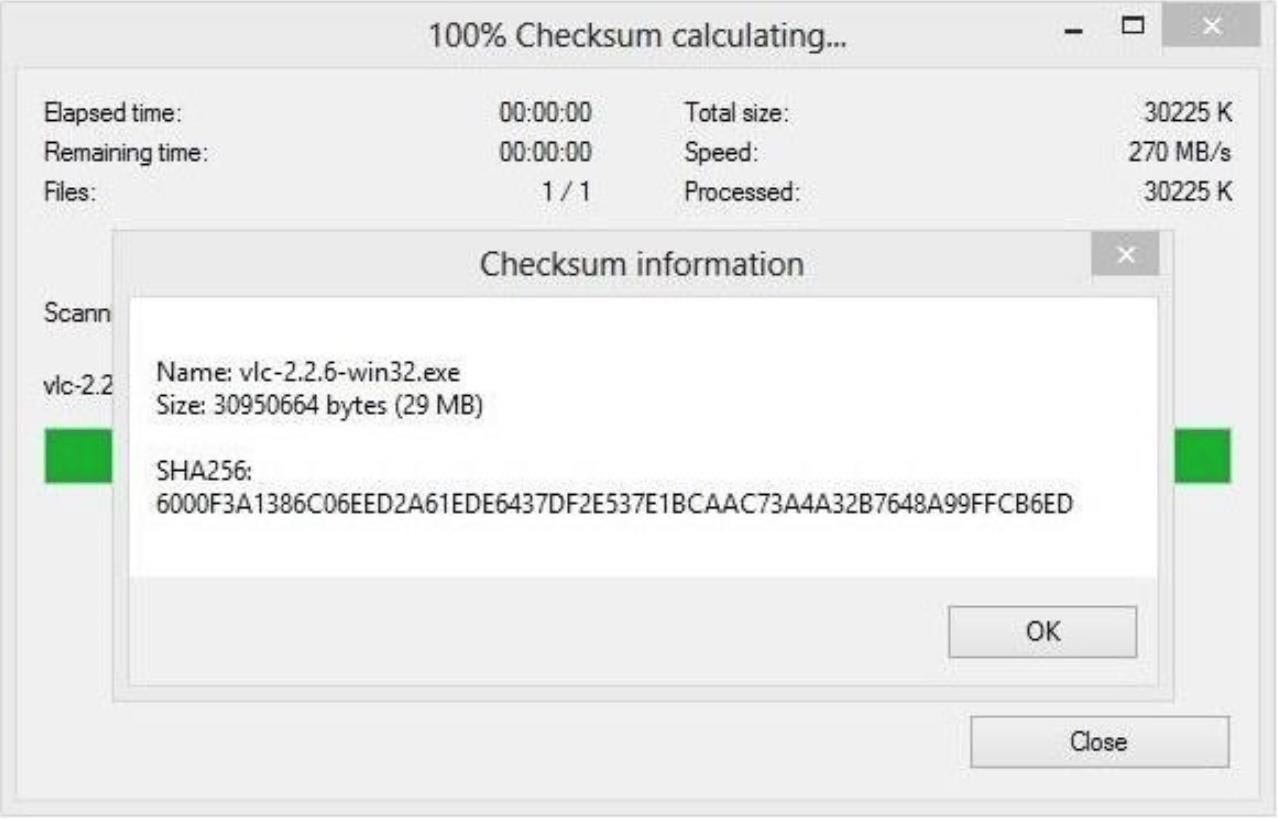
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens

Steve on Twitter: "SHA-256 is one of the best methods I know of to protect passwords, but just to be safe use SHA-512.</sarcasm> Use bcrypt ($2b$… or $2y$…). You can't go wrong
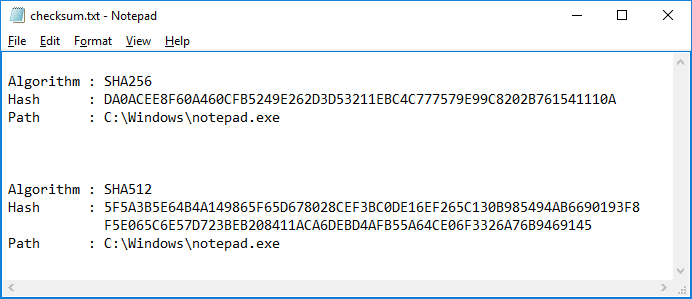
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens
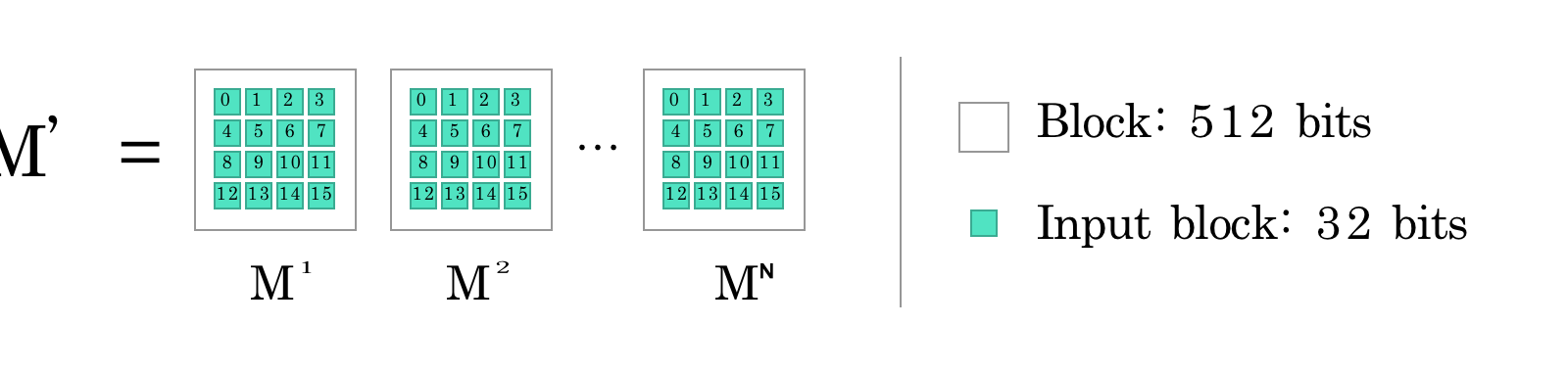



![SHA-256.IO [BEST CLOUD MINING PLATFORM ON INTERNET] | by PAWN SHOP RICK | Jan, 2021 | Medium SHA-256.IO [BEST CLOUD MINING PLATFORM ON INTERNET] | by PAWN SHOP RICK | Jan, 2021 | Medium](https://miro.medium.com/max/899/0*8YUOD7Fk_MGSIyFc.png)