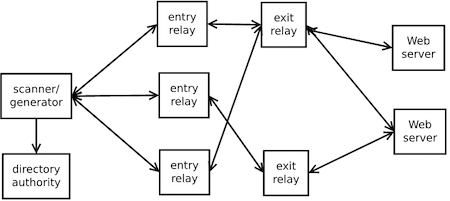
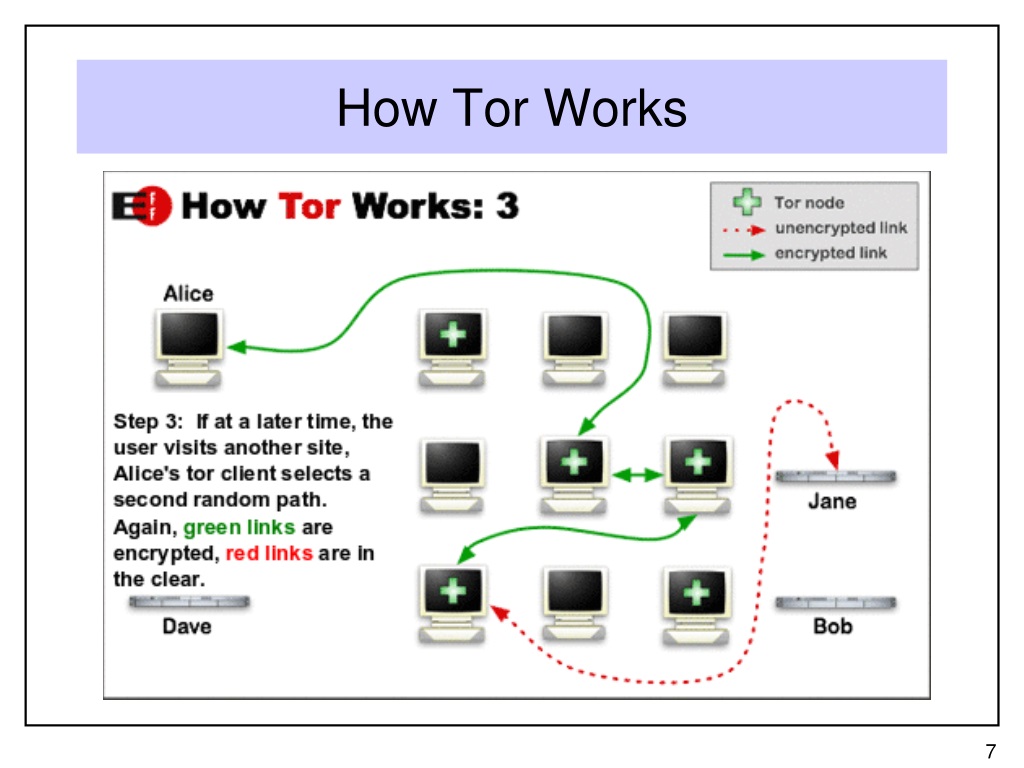
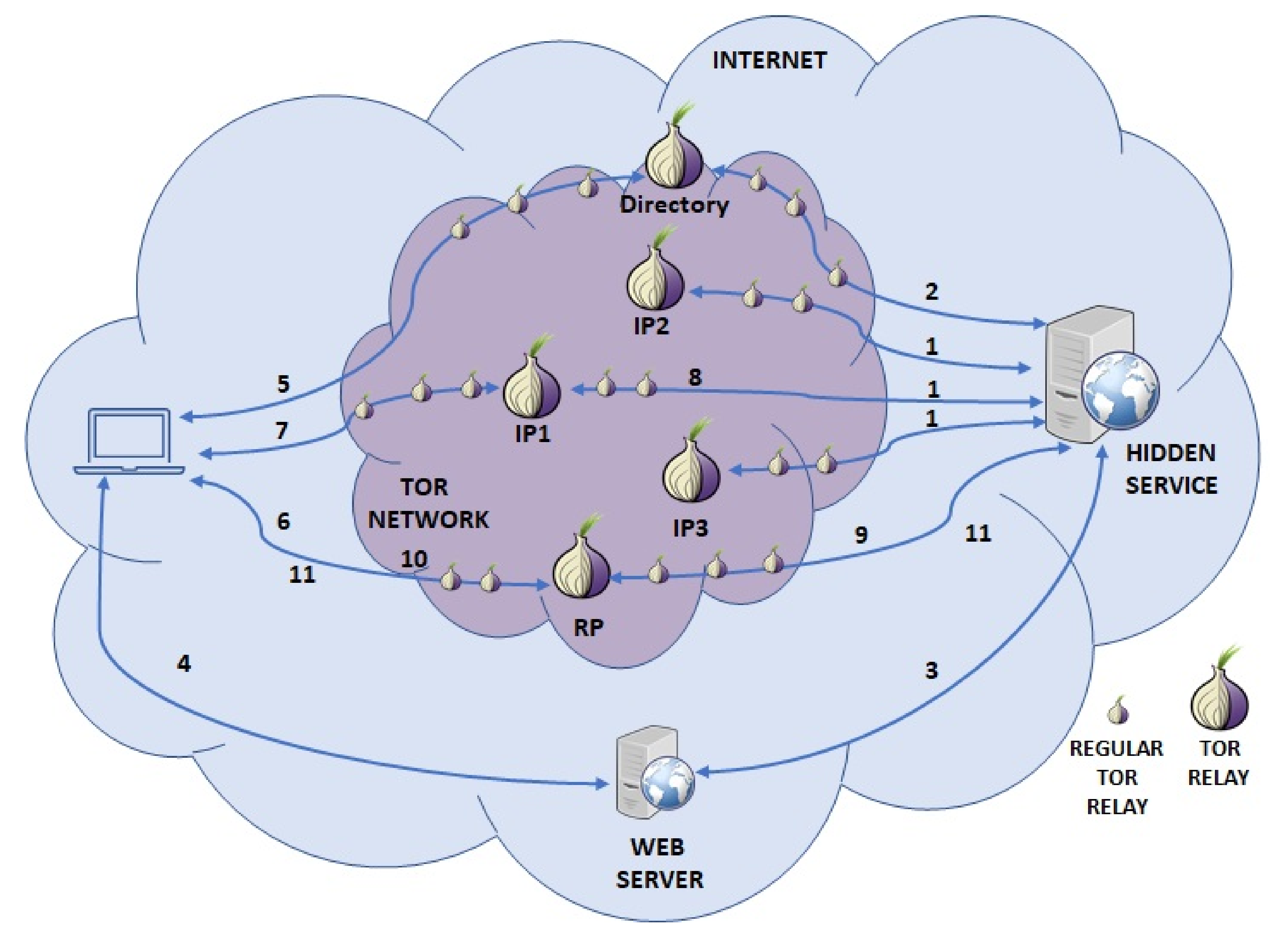
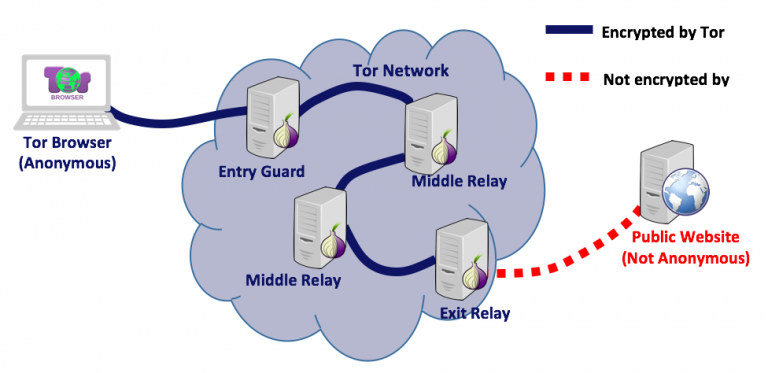
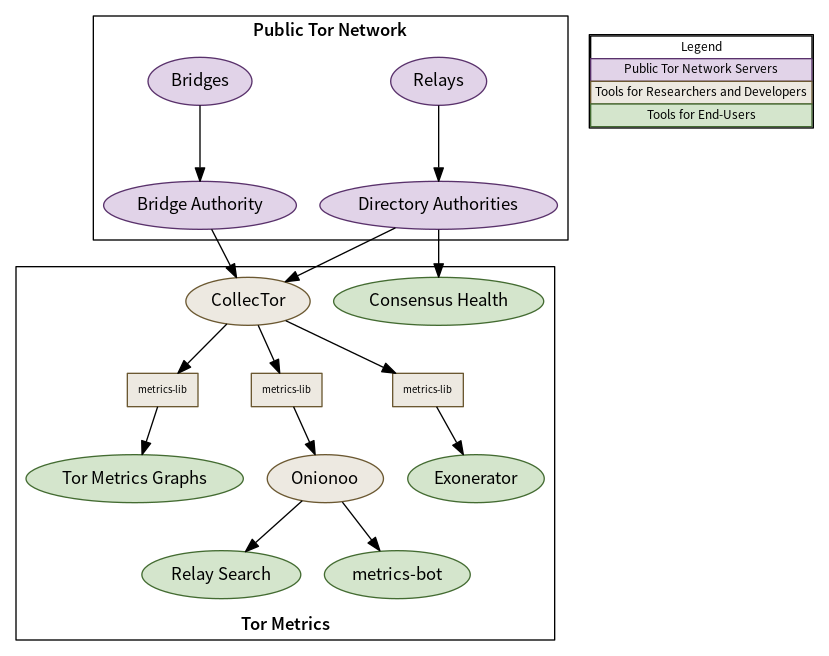
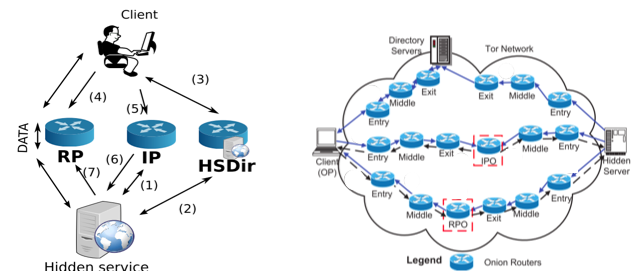
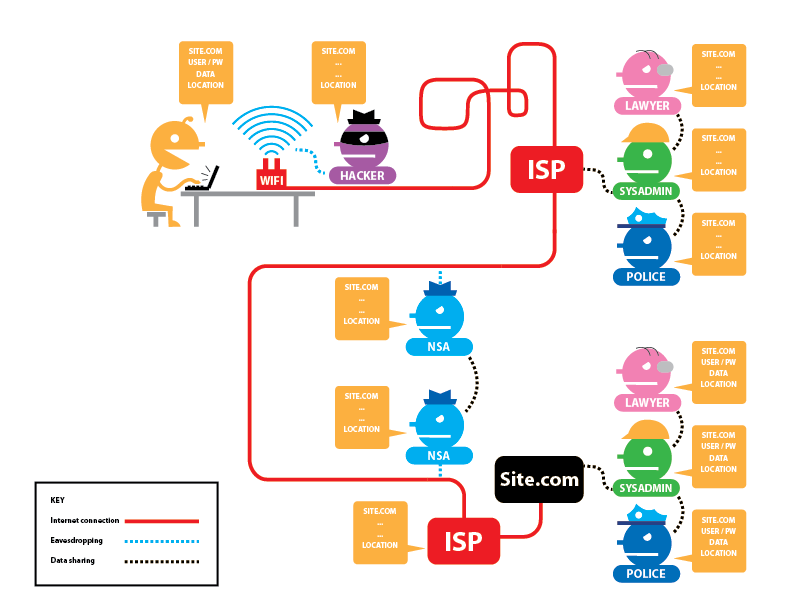
Predicting Tor Path Compromise by Exit Port IEEE WIDA 2009December 16, 2009 Kevin Bauer, Dirk Grunwald, and Douglas Sicker University of Colorado Client. - ppt download

A novel application classification attack against Tor - He - 2015 - Concurrency and Computation: Practice and Experience - Wiley Online Library