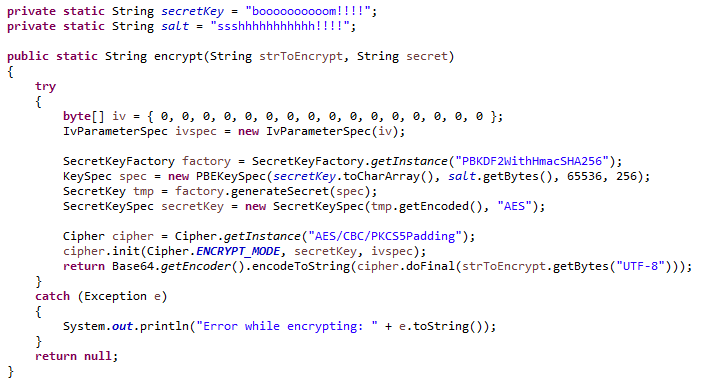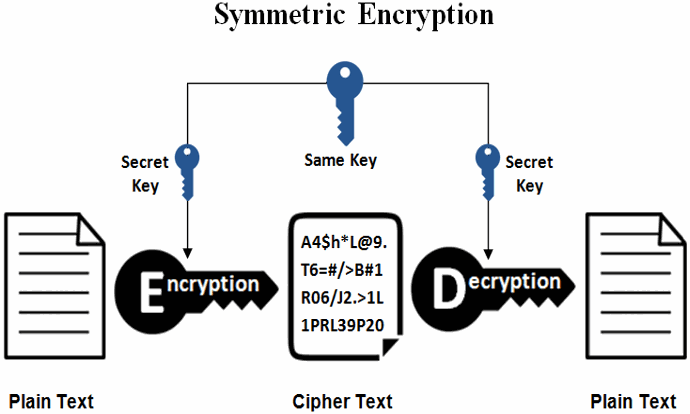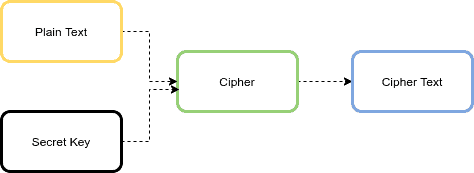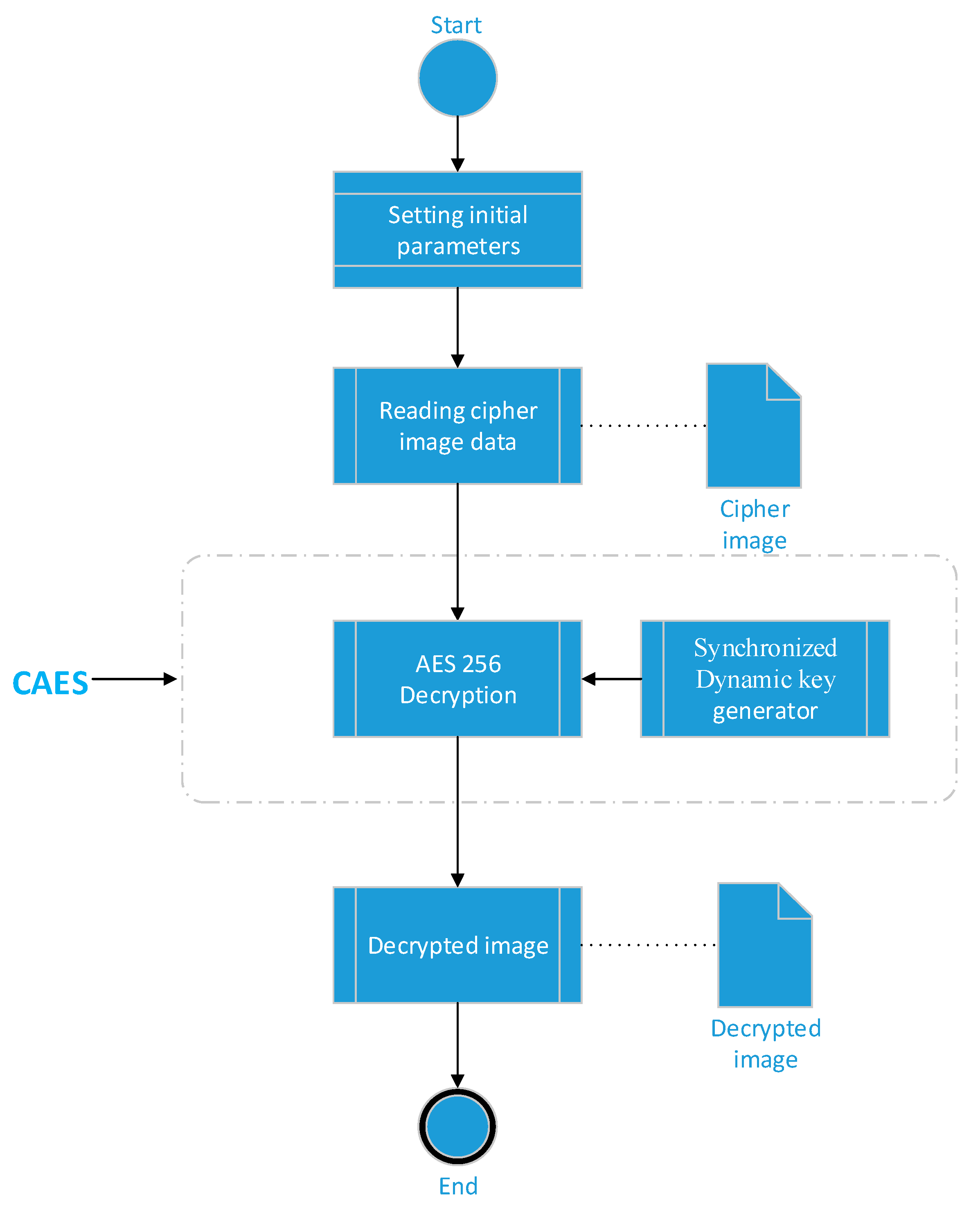
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm | HTML
Generating an Encryption Key Without A Pass Phrase — Meet ECIES | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium







![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/aes%20algorithm%20working%20opt.jpg?width=1002&name=aes%20algorithm%20working%20opt.jpg)